The department of health along with human services requires all the organizations to handle health information that is protected. This also includes HIPAA hosting providers which are helpful in conducting an analysis of risk. This is the first step towards the implementation of safeguards which is specified in the security rule of HIPAA. This further ultimately achieves HIPAA compliance. The standards guide entails nine components that need to be included mandatorily. It is extremely important for you to know whether your company is prepared with an adequate security HIPAA risk analysis and compliance audit or not. Following are the steps that need to be followed in case of keeping up with the requirements.
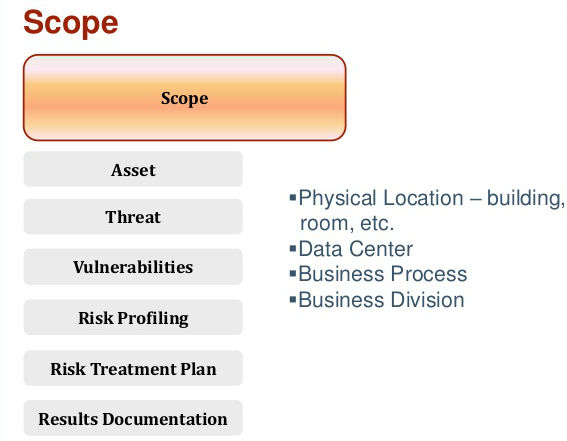
Scope of the Analysis –
Any kind of potential risks or any vulnerability caused to the privacy along with availability and integration of ePHI. This further includes all the electronic media that the organization uses for the creation, receiving, maintenance and transmission of ePHI. This includes desktops, portable media and networks. The network security present between varied multiple locations are extremely important for including in the scope of the analysis. It also includes aspects of your HIPAA hosting terms along with a third party or even business associate.
Data Collection
It is extremely important to locate where the data gets stored, received, maintained and transmitted. Also, if health information is being hosted by you at HIPAA data center, then you need to contact the hosting provider in order to document where and how the data is being stored. HIPAA compliance training helps the company function better in these tasks.
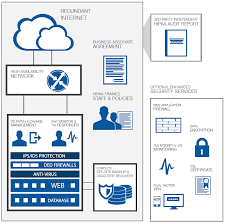
Assess the Current Measures of Security
Right from a technical perspective, it might include any encryption, two-factor authentication along with security methods which are put in place by the HIPAA hosting provider.
Determine the Chances of Occurrence of Threat
By the use of qualitative or quantitative methods, you can assess the maximum impact of the threat of a
data caused to the organization. It is important to note down the number of people who can be affected and to what extent private data can be exposed. This can save your company from impending threats, thus helping in HIPAA risk analysis.
Evaluate the Level of Risk
Your company needs to take into consideration the average of the assigned likelihood along with its impact levels in order to determine the level of risk. The risk levels should further be accompanied by a thorough list of corrective actions which is performed in order to mitigate the risks.
Finalize Documentation
You also need to write everything in an extremely organized manner. In order to be prepared with security measures, you need to write the analysis.
Provide periodic Review Along with Updates of the Risk Assessment
It is very important to conduct the risk analysis on a regular basis. While there is no required timeline, it is recommended that the organizations conduct a risk analysis whenever your company plans or implements to adopt fresh new technology or business operations. This includes the switching of the methods of data storage right from managed servers to cloud computing. It also includes ownership or turnover of key staff.
Training
It is important to provide HIPAA compliance training to help the employees and the company deal with any risk or impending threats.